« Security/Crypt/USBKey » : différence entre les versions
(Page créée avec « '''USB stick encryption using Linux''' = Introduction = In case you will loose your USB stick, all data stored on it will be lost and what is more important they will be mo... ») |
|||
| Ligne 30 : | Ligne 30 : | ||
mkfs -t ext4 /dev/sdc1 | mkfs -t ext4 /dev/sdc1 | ||
</syntaxhighlight> | </syntaxhighlight> | ||
= Write random data = | = Write random data = | ||
Dernière version du 19 décembre 2012 à 12:08
USB stick encryption using Linux
Introduction
In case you will loose your USB stick, all data stored on it will be lost and what is more important they will be most likely in hands of some other person which will then have an access to your private information and use this information in any way s/he sees fit. This is one of many fears of USB stick users. One solution which can be easily applied is to not to store any private information on USB stick, however this will diminish a prime usage of your USB stick to a bare minimum as all non-private data usually do not have to be stored on USB since they can be almost always downloaded anytime and anywhere from the Internet. Another solution is to encrypt your USB stick so it will be accessible only to those users who posses a correct password which will fit to decrypt an used encryption method. This article will deal with the second solution and that is encryption of an USB stick device.
Although encrypting an USB stick seems to be the best and easiest solution it must be said that it also comes with number of disadvantages. The first disadvantage is that decryption of the USB key must be done using a Linux system with kernel version 2.6 and higher which has a "dm_crypt" module loaded in the running kernel. In other words, you cannot use your encrypted USB stick on any Windows machine and UNIX-like system with kernel version below 2.6. Therefore, to encrypt only a part of USB stick which holds only a private information seems to be a good solution. In this article we will use USB stick of capacity 16GB known to the system as a block device /dev/sdc. We first partition the disk to hold two partitions, one for encrypted data and the other for non-private data and then encrypt only single partition intended to hold private data.
Partitioning an USB stick
Let's start with partitioning of our USB stick. Insert your USB stick into PC's USB slot
Search the output of parted command and retrieve a Disk's file name of your USB stick. As it was already mentioned before, in this article we will use /dev/sdc. Once we have a file name of our USB stick we can create partitions to be used for encryption and for storage of non-private data. In my case I will split the USB stick into two partitions, first with size of 100MB and the rest of the space will be used to create second partition and this will produce /dev/sdc1 and /dev/sdc2 respectively.
We had created a primary partition with ext4 file system and size of 100MB and this partition ( /dev/sdc1 ) will be used to store no-encrypted data. And so, we had created a second partition and this partition ( /dev/sdc2 ) will be used to store encrypted data starting from 100MB up to last sector. The first partition will serve as a general storage ( pam_usb ). The final look of your USB stick partition table may look similar to the one below:
Disk /dev/sdc: 2004 Mo, 2004877312 bytes
62 heads, 62 sectors/track, 1018 cylinders
Units = cylinders of 7648 * 512 = 3915776 bytes
Disk identifier: 0x04f71742
Device Boot Start End Blocks Id System
/dev/sdc1 2048 206847 102400 83 Linux
/dev/sdc2 206848 3915775 1854464 83 Linux
Create file system on no-encrypted partition
mkfs -t ext4 /dev/sdc1
Write random data
To avoid pattern based encryption attacks it is advisable to write some random data to a partition before proceeding with an encryption. The following dd command can be used to write such data to your partition. It may take some time. Time depends on the entropy data generated by your system:
dd bs=4K if=/dev/urandom of=/dev/sdc2
Partition encryption
Now it is time to encrypt a newly created partition. For this purpose we will use cryptsetup tool. If cryptsetup command is not available on your system make sure that cryptsetup package installed. The following command will encrypt /dev/sdc1 partiton with 256-bit AES XTS algorithm. This algorithm is available on any kernel with version higher than 2.6.24.
cryptsetup -h sha256 -c aes-xts-plain -s 256 luksFormat /dev/sdc2
WARNING!
========
This will overwrite data on /dev/sdc2 irrevocably.
Are you sure? (Type uppercase yes): YES
Enter LUKS passphrase:
Verify passphrase:
Command successful.
Mounting USB partition and decryption
In the next step we will set name of our encrypted partition to be recognized by the system's device mapper. You can choose any name. For example we can use name "private":
cryptsetup luksOpen /dev/sdc2 private
Enter LUKS passphrase:
After executing this command your encrypted partition will be available to your system as /dev/mapper/private. Now we can create file system and mount the partition to /mnt/private and make it accessible to your self:
mkfs -t ext4 /dev/mapper/private
Create a mount point and mount a partition:
mkdir /mnt/private
mount /dev/mapper/private /mnt/private
chown -R didier:didier /mnt/private
Now your encrypted partition is available in /mnt/private directory. If you do not wish to have an access to your USB stick's encrypted partition anymore you need to first unmount it from the system and then use cryptsetup command to close the connected protection.
umount /mnt/private
cryptsetup luksClose /dev/mapper/private
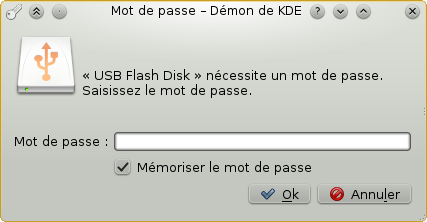
Desktop mount of an encrypted USB partition
Your desktop may react to an encrypted partition by pop-up dialog to prompt you to enter a password for your encrypted partition as is it in case of Fedora for example.
However, some Linux systems may not provide any facility to mount encrypted partitions and you would have to do it manually ( see section "Mounting USB encrypted partition" for details ). In any case make sure that you have cryptsetup package installed and thus md_crypt module loaded in to the running kernel in order to use your encrypted USB stick.