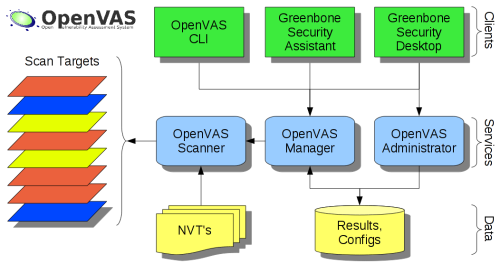
IDS/OpenVas
OpenVAS ( Open Vulnerability Assessment System ) est une suite d'outils qui permet de scanner et solutionner les vulnérabilités d'un réseau.
Le scanner actuel est accompagné de nombreux tests ( Network Vulnerability Tests: NVTs ) avec une fréquence de mise à jour journalière et comportent pas moins de 25 000 tests au total ( mai 2012 )
Description
Tous les composants d'OpenVAS sont libres et la plupart sont disponible sous la license GNU ( General Public License ).
- librairies: bibliothèques communes aux outils OpenVAS.
- scanner: Service qui évalue techniquement les vulnérabilités. Il se positionne entre la cible et le service de pilotage ( manager ).
- manager: C'est la pierre angulaire de lasuite. Il controle le scanner, récupère les résultats, agrège, stocke et interprète ceux-ci.
- administrator: service permettant d'administrer les comptes utilisés pour l'exploitation de la suite OpenVAS et de mettre à jour la base des vulnérabilités.
Installation
yum install openvas-client openvas-libraries openvas-manager openvas-scanner openvas-manager-sysvinit openvas-scanner-sysvinit openvas-administrator openvas-administrator-sysvinit openvas-cli greenbone-security-assistant
Si OpenVAS a déjà été installé, on peut nettoyer avec ce script
yum erase openvas-client openvas-libraries openvas-manager openvas-scanner openvas-manager-sysvinit openvas-scanner-sysvinit openvas-administrator openvas-administrator-sysvinit openvas-cli greenbone-security-assistant gsd
rm -rf /var/lib/openvas
rm -rf /var/log/openvas
rm -rf /var/cache/openvas
rm -rf /etc/openvas
rm -rf /etc/pki/openvas
Setup
openvas-check-setup
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
openvas-check-setup 2.1.5
Test completeness and readiness of OpenVAS-4
(add '--v5' if you want to check for OpenVAS-5)
Please report us any non-detected problems and
help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Send us the log-file (/tmp/openvas-check-setup.log) to help analyze the problem.
Use the parameter --server to skip checks for client tools
like GSD and OpenVAS-CLI.
Step 1: Checking OpenVAS Scanner ...
OK: OpenVAS Scanner is present in version 3.2.5.
ERROR: No CA certificate file of OpenVAS Scanner found.
FIX: Run 'openvas-mkcert'.
ERROR: Your OpenVAS-4 installation is not yet complete!
Please follow the instructions marked with FIX above and run this
script again.
If you think this result is wrong, please report your observation
and help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Please attach the log-file (/tmp/openvas-check-setup.log) to help us analyze the problem.
Création de l'autorité de certification
openvas-mkcert
-------------------------------------------------------------------------------
Creation of the OpenVAS SSL Certificate
-------------------------------------------------------------------------------
This script will now ask you the relevant information to create the SSL certificate of OpenVAS.
Note that this information will *NOT* be sent to anybody (everything stays local), but anyone with the ability to connect to your OpenVAS daemon will be able to retrieve this information.
CA certificate life time in days [1460]:
Server certificate life time in days [365]:
Your country (two letter code) [DE]: FR
Your state or province name [none]: PACA
Your location (e.g. town) [Berlin]: Cavaillon
Your organization [OpenVAS Users United]: B2PWeb
-------------------------------------------------------------------------------
Creation of the OpenVAS SSL Certificate
-------------------------------------------------------------------------------
Congratulations. Your server certificate was properly created.
The following files were created:
. Certification authority:
Certificate = /etc/pki/openvas/CA/cacert.pem
Private key = /etc/pki/openvas/private/CA/cakey.pem
. OpenVAS Server :
Certificate = /etc/pki/openvas/CA/servercert.pem
Private key = /etc/pki/openvas/private/CA/serverkey.pem
Press [ENTER] to exit
Mise à jour des plugins
On va télécharger une archive pour que la synchronisation soit plus rapide et la décompresser dans <path>/var/lib/openvas/plugins</path>
cd /tmp
wget http://www.openvas.org/openvas-nvt-feed-current.tar.bz2
cd /var/lib/openvas/plugins
tar xjf /tmp/openvas-nvt-feed-current.tar.bz2
Maintenant on lance la synchronisation des plugins
openvas-nvt-sync [i] This script synchronizes an NVT collection with the 'OpenVAS NVT Feed'. [i] The 'OpenVAS NVT Feed' is provided by 'The OpenVAS Project'. [i] Online information about this feed: 'http://www.openvas.org/openvas-nvt-feed.html'. [i] NVT dir: /var/lib/openvas/plugins [i] Will use rsync [i] Using rsync: /bin/rsync [i] Configured NVT rsync feed: rsync://feed.openvas.org:/nvt-feed OpenVAS feed server - http://openvas.org/ This service is hosted by Intevation GmbH - http://intevation.de/ All transactions are logged. Please report problems to admin@intevation.de receiving incremental file list ./ sent 39 bytes received 909710 bytes 259928.29 bytes/sec total size is 138278677 speedup is 152.00 [i] Checking dir: ok [i] Checking MD5 checksum: ok
On recheck
openvas-check-setup
openvas-check-setup 2.1.5
Test completeness and readiness of OpenVAS-4
(add '--v5' if you want to check for OpenVAS-5)
Please report us any non-detected problems and
help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Send us the log-file (/tmp/openvas-check-setup.log) to help analyze the problem.
Use the parameter --server to skip checks for client tools
like GSD and OpenVAS-CLI.
Step 1: Checking OpenVAS Scanner ...
OK: OpenVAS Scanner is present in version 3.2.5.
OK: OpenVAS Scanner CA Certificate is present as /etc/pki/openvas/CA/cacert.pem.
OK: NVT collection in /var/lib/openvas/plugins contains 27523 NVTs.
WARNING: Signature checking of NVTs is not enabled in OpenVAS Scanner.
SUGGEST: Enable signature checking (see http://www.openvas.org/trusted-nvts.html).
Step 2: Checking OpenVAS Manager ...
OK: OpenVAS Manager is present in version 2.0.4.
ERROR: No client certificate file of OpenVAS Manager found.
FIX: Run 'openvas-mkcert-client -n om -i'
ERROR: Your OpenVAS-4 installation is not yet complete!
Please follow the instructions marked with FIX above and run this
script again.
If you think this result is wrong, please report your observation
and help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Please attach the log-file (/tmp/openvas-check-setup.log) to help us analyze the problem.
Création du certificat client
Le manager doit s'authentifier auprès du scanner. Cela est réalisé via le certificat d'un utilisateur nommé om. Désolé pour les fans du PSG.
openvas-mkcert-client -i This script will now ask you the relevant information to create the SSL client certificates for OpenVAS. Client certificates life time in days [365]: Your country (two letter code) [DE]: FR Your state or province name [none]: PACA Your location (e.g. town) [Berlin]: Cavaillon Your organization [none]: B2PWeb Your organizational unit [none]: SRS ********** We are going to ask you some question for each client certificate. If some question has a default answer, you can force an empty answer by entering a single dot '.' ********* OpenVAS username for the new user: om Client certificates life time in days [365]: Country (two letter code) [FR]: State or province name [PACA]: Location (e.g. town) [Cavaillon]: Organization [B2PWeb]: Organization unit [SRS]: e-Mail []: srs@b2pweb.com Generating RSA private key, 1024 bit long modulus ...........................++++++ ..........++++++ e is 65537 (0x10001) You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [DE]:State or Province Name (full name) [Some-State]:Locality Name (eg, city) []:Organization Name (eg, company) [Internet Widgits Pty Ltd]:Organizational Unit Name (eg, section) []:Common Name (eg, your name or your server's hostname) []:Email Address []:Using configuration from /tmp/openvas-mkcert-client.14759/stdC.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'FR' stateOrProvinceName :PRINTABLE:'PACA' localityName :PRINTABLE:'Cavaillon' organizationName :PRINTABLE:'B2PWeb' organizationalUnitName:PRINTABLE:'SRS' commonName :PRINTABLE:'om' emailAddress :IA5STRING:'srs@b2pweb.com' Certificate is to be certified until Sep 4 09:58:50 2013 GMT (365 days) Write out database with 1 new entries Data Base Updated User rules ---------- openvassd has a rules system which allows you to restrict the hosts that has the right to test. For instance, you may want him to be able to scan his own host only. Please see the openvas-adduser(8) man page for the rules syntax. Enter the rules for this user, and hit ctrl-D once you are done: (the user can have an empty rules set) Admin User om added to OpenVAS.
On recheck
openvas-check-setup
openvas-check-setup 2.1.5
Test completeness and readiness of OpenVAS-4
(add '--v5' if you want to check for OpenVAS-5)
Please report us any non-detected problems and
help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Send us the log-file (/tmp/openvas-check-setup.log) to help analyze the problem.
Use the parameter --server to skip checks for client tools
like GSD and OpenVAS-CLI.
Step 1: Checking OpenVAS Scanner ...
OK: OpenVAS Scanner is present in version 3.2.5.
OK: OpenVAS Scanner CA Certificate is present as /etc/pki/openvas/CA/cacert.pem.
OK: NVT collection in /var/lib/openvas/plugins contains 27523 NVTs.
WARNING: Signature checking of NVTs is not enabled in OpenVAS Scanner.
SUGGEST: Enable signature checking (see http://www.openvas.org/trusted-nvts.html).
Step 2: Checking OpenVAS Manager ...
OK: OpenVAS Manager is present in version 2.0.4.
OK: OpenVAS Manager client certificate is present as /etc/pki/openvas/CA/clientcert.pem.
ERROR: No OpenVAS Manager database found. (Tried: /var/lib/openvas/mgr/tasks.db)
FIX: Run 'openvasmd --rebuild' while OpenVAS Scanner is running.
ERROR: Your OpenVAS-4 installation is not yet complete!
Please follow the instructions marked with FIX above and run this
script again.
If you think this result is wrong, please report your observation
and help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Please attach the log-file (/tmp/openvas-check-setup.log) to help us analyze the problem.
Démarrage manuel d'OpenVAS
On doit donc démarrer le scanner puis lancer la commande openvasmd --rebuild. Le premier démarrage du scanner peut être très (trop) long car il va mettre en cache les plugins.
openvassd --listen=127.0.0.1 --port=9391
Reconstruction de la base des plugins
openvasmd --rebuild
Lancement du manager
openvasmd --listen=127.0.0.1 --port=9390 --slisten=127.0.0.1 --sport=9391
Lancement de l'administrator
openvasad --listen=127.0.0.1 --port=9393 --enable-modify-settings --sync-script=/usr/sbin/openvas-nvt-sync
Lancement de Greenbone Security Assistant
gsad --listen=127.0.0.1 --port=9392 --alisten=127.0.0.1 --aport=9393 --mlisten=127.0.0.1 --mport=9390 --ssl-private-key=/etc/pki/openvas/private/CA/serverkey.pem --ssl-certificate=/etc/pki/openvas/CA/servercert.pem
ln -s /etc/pki/openvas/* /var/lib/openvas/
On peut maintenant vérifier la bonne installation d'OpenVAS
openvas-check-setup
openvas-check-setup 2.1.5
Test completeness and readiness of OpenVAS-4
(add '--v5' if you want to check for OpenVAS-5)
Please report us any non-detected problems and
help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Send us the log-file (/tmp/openvas-check-setup.log) to help analyze the problem.
Use the parameter --server to skip checks for client tools
like GSD and OpenVAS-CLI.
Step 1: Checking OpenVAS Scanner ...
OK: OpenVAS Scanner is present in version 3.2.5.
OK: OpenVAS Scanner CA Certificate is present as /etc/pki/openvas/CA/cacert.pem.
OK: NVT collection in /var/lib/openvas/plugins contains 27523 NVTs.
WARNING: Signature checking of NVTs is not enabled in OpenVAS Scanner.
SUGGEST: Enable signature checking (see http://www.openvas.org/trusted-nvts.html).
Step 2: Checking OpenVAS Manager ...
OK: OpenVAS Manager is present in version 2.0.4.
OK: OpenVAS Manager client certificate is present as /etc/pki/openvas/CA/clientcert.pem.
OK: OpenVAS Manager database found in /var/lib/openvas/mgr/tasks.db.
OK: Access rights for the OpenVAS Manager database are correct.
OK: sqlite3 found, extended checks of the OpenVAS Manager installation enabled.
OK: OpenVAS Manager database is at revision 41.
OK: OpenVAS Manager expects database at revision 41.
OK: Database schema is up to date.
OK: OpenVAS Manager database contains information about 27523 NVTs.
OK: xsltproc found.
Step 3: Checking OpenVAS Administrator ...
OK: OpenVAS Administrator is present in version 1.1.2.
OK: At least one user exists.
OK: At least one admin user exists.
Step 4: Checking Greenbone Security Assistant (GSA) ...
OK: Greenbone Security Assistant is present in version 2.0.1.
Step 5: Checking OpenVAS CLI ...
OK: OpenVAS CLI version 1.1.5.
Step 6: Checking Greenbone Security Desktop (GSD) ...
OK: Greenbone Security Desktop is present in Version 1.2.2.
Step 7: Checking if OpenVAS services are up and running ...
OK: netstat found, extended checks of the OpenVAS services enabled.
OK: OpenVAS Scanner is running and listening on all interfaces.
OK: OpenVAS Scanner is listening on port 9391, which is the default port.
OK: OpenVAS Manager is running and listening on all interfaces.
OK: OpenVAS Manager is listening on port 9390, which is the default port.
OK: OpenVAS Administrator is running and listening on all interfaces.
OK: OpenVAS Administrator is listening on port 9393, which is the default port.
OK: Greenbone Security Assistant is running and listening on all interfaces.
OK: Greenbone Security Assistant is listening on port 9392, which is the default port.
Step 8: Checking nmap installation ...
WARNING: Your version of nmap is not fully supported: 6.01
SUGGEST: You should install nmap 5.51.
Step 9: Checking presence of optional tools ...
OK: pdflatex found.
OK: PDF generation successful. The PDF report format is likely to work.
OK: ssh-keygen found, LSC credential generation for GNU/Linux targets is likely to work.
OK: rpm found, LSC credential package generation for RPM based targets is likely to work.
WARNING: Could not find alien binary, LSC credential package generation for DEB based targets will not work.
SUGGEST: Install alien.
WARNING: Could not find makensis binary, LSC credential package generation for Microsoft Windows targets will not work.
SUGGEST: Install nsis.
It seems like your OpenVAS-4 installation is OK.
If you think it is not OK, please report your observation
and help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Please attach the log-file (/tmp/openvas-check-setup.log) to help us analyze the problem.
Démarrage automatique d'OpenVAS
Edition du fichier /etc/sysconfig/gsad
# # The file to use as private key for HTTPS # GSA_SSL_PRIVATE_KEY=/etc/pki/openvas/private/CA/serverkey.pem # # The file to use as certificate for HTTPS # GSA_SSL_CERTIFICATE=/etc/pki/openvas/CA/servercert.pem